Web Sign-In for Windows
- Yanko Arsov

- Jan 29, 2024
- 4 min read
Updated: Jan 29, 2024
Recently, there was a request to enable the Windows Web sign-in option in a production environment which triggered a discussion on its usefulness. The need to prevent cyberattacks in today's digital world results in the implementation of highly secure technologies, such as Windows Hello and Security Keys. The inclusion of Windows Web sign-in stands as another effective solution within this set further enhancing the capabilities of secure login.
With the introduction of KB5030310 (Windows 11, version 22H2), the web-based sign-in option is now available for Microsoft Entra joined devices. To be precise, this option was previously accessible on Windows 10 devices with the support for Temporary Access Pass (TAP) only, but it has now been enhanced with additional functionalities in Windows 11.
First, it is good to note that Web sign-in does not appear on the screen by default. It needs to be configured explicitly. Enabling this feature is a simple operation that can be achieved with just a few clicks using Intune, non-Microsoft MDM tools by configuring custom policy or by deploying a provisioning package. There is nothing specific to point out as the process is well-documented by Microsoft and works seamlessly. For detailed instructions we can refer to the Microsoft documentation.
After configuring Web sign-in, a new icon appears on the login screen:
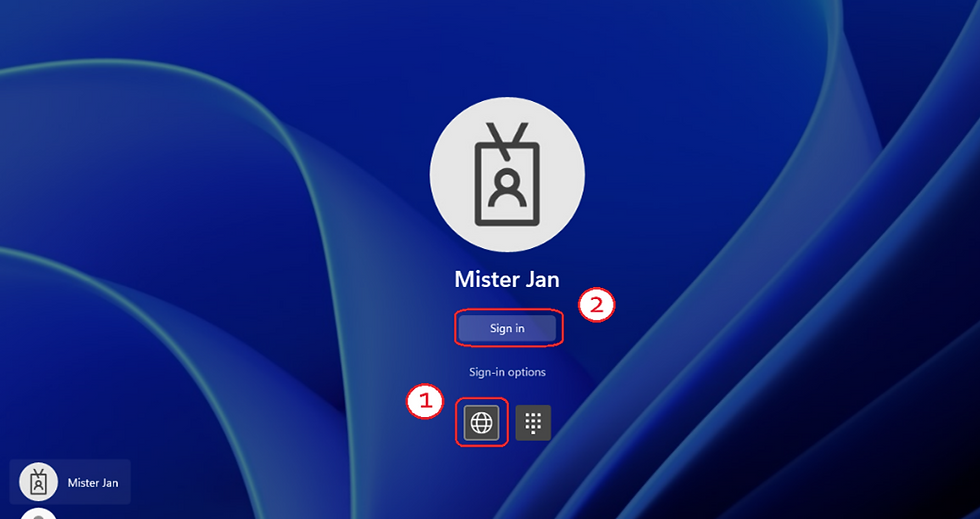
The user clicks on the „Web sign-in“ icon.
The „Sign in“ button must be selected as well.
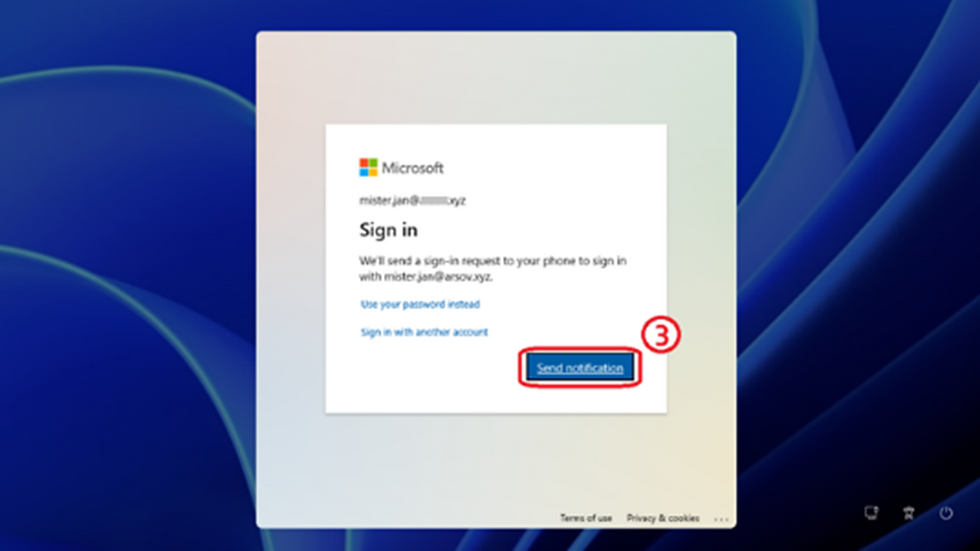
An authentication popup window appears on the screen. Select the "Send notification" button and then follow the instructions on your mobile device.
Note: It is highly recommended to implement passwordless authentication together with the Web sign-in. The Microsoft Authenticator mobile app can be utilised for both work or school and personal Microsoft accounts, enabling passwordless sign-ins.
Let's explore the benefits of using web sign-in and discover the elements that can capture one's interest. Initially, it presents itself as a contemporary and stylish Windows authentication solution but what distinguishes it and makes it preferable compared to others? I cannot accept that it is just a new icon on the sign-in screen. Let's take a closer look on some features related to Web Sign-in:
As previously mentioned, it can be configured as a modern and effective passwordless solution.
It is a handy feature for PIN reset.
Another option involves utilising Web Sign-in in conjunction with Temporary Access Pass (TAP) limited to max 8 hours. This approach proves beneficial in scenarios where, for example, an engineer can offer support without accessing the user's account directly or in cases of a lost FIDO2 security key or malfunctioning Windows Hello.
However, there's another feature that has captured my attention and interest – the scenario where the Microsoft Entra ID tenant is federated with a third-party SAML identity provider. This presents an ideal situation for leveraging Web sign-in. Consider the common case of mergers and acquisitions where the consolidation of environments is a time-consuming process. Often, there are no prepared plans or budgets for immediate migrations at the merger date. In some scenarios users can be provided with devices that are already part of the new or target environment (Entra joined devices). In this context both environments could be federated allowing users to leverage their former credentials to sign-in to the new devices. This streamlined approach not only simplifies the transition but also ensures prompt and seamless collaboration among users from various acquired departments.
I would like to mention that certain features present drawbacks. For instance, if the device is offline the user cannot utilise Web sign-in since cached credentials are not supported. The sign-in takes relatively long time compared to the other options. This is understandable given that it generates internet traffic. It is also a bit annoying for me that after selecting the Web Sign-in icon an additional click on the "Sign-in" button is necessary. It would be more convenient if the credentials field appeared directly after the first click. These are minor details that do not compromise the overall functionality of the feature.
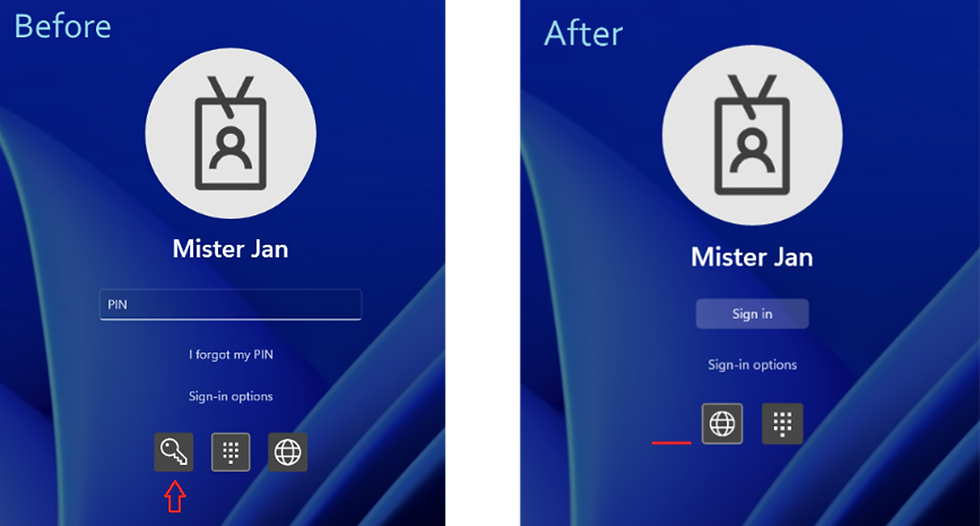
While considering Windows Web sign-in as a potential passwordless authentication solution, I'd like to highlight another notable feature that can be implemented in conjunction – Windows Passwordless Experience security policy. As Microsoft states, with this option users:
Cannot use the password credential provider on the Windows lock screen.
Are not prompted to use a password during in-session authentications (for example, UAC elevation, password manager in the browser, etc.)
Do not have the option Accounts > Change password in the Settings app.
The policy cannot prevent people from using passwords entirely, but it definitely guides them to a secure way of thinking by hiding the password icon. That is why it might be beneficial to consider it.
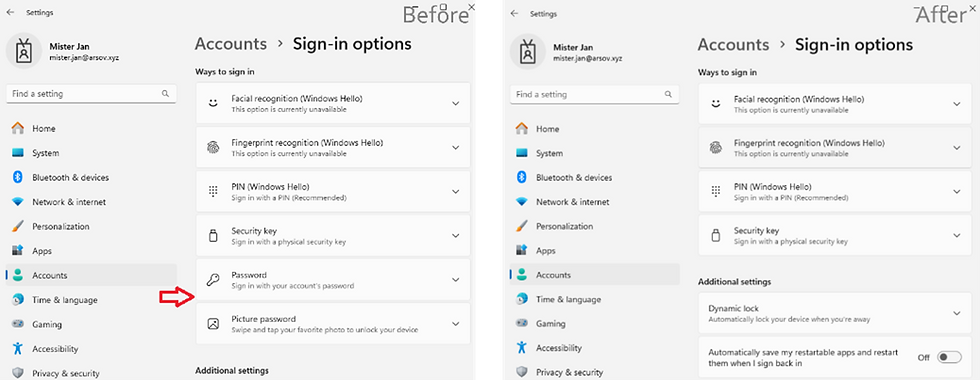
The result is also visible within the accounts‘ „sign-in“ area in Windows settings. After the implementation of the passwordless experience security policy the password sections are missing:
Conclusion
The Windows Web Sign-in option and its potential to unlock new possibilities in secure authentication, I would argue that it depends on the specifics and circumstances of each individual case. It certainly does not pose any harm and provides us with another authentication mechanism that we can rely on.
At NUWEY we consult companies on the authentication mechanisms and solutions that make most sense to their businesses. Contact us if you are not sure what solution to implement, or if you need a team of experts to help with the transition from one authentication provider to another.




Comments